WTH are Azure AD Security Defaults?
Security Defaults are a new feature in Azure AD that was introduced in October 2019; however, I have found that not many people are aware of this feature, which can be really useful if you are on the Azure AD free tier. Given that, I thought it was worthy of its own WTH article.
What are Azure AD Security Defaults?
Security Defaults are an attempt by Microsoft to try and make Azure AD more secure by default, particularly for users of the free tier. If you pay for Azure AD Premium licences, you can do lots of things with security rules by using conditional access, but this is not available in the free tier. Security defaults aim to take some of these security rules and allow you to apply them to your free subscription.
One of the big selling points for security defaults is that it brings multi-factor authentication to your users for free. There are some limitations around this which will discuss, but this service does allow you to get MFA with no additional cost. Previously this would have required either Azure AD P1 licences, or pay per use MFA. This is a big benefit for free users and will bring a significant extra level of security. This encompasses both Azure and Office 365.
Along with MFA, security defaults also applies several other policies that make your tenant more secure:
- Requiring all users to sign up for MFA (for free)
- Requiring those in Azure administrator roles to perform MFA
- Blocking legacy authentication protocols - this includes clients that don’t use modern authentication and so don’t support MFA, and older mail protocols like IMAP, SMTP and POP3
- Requiring MFA authentication when undertaking privileged actions using the Azure portal, PowerShell or CLI
Security defaults are very much designed for users on the Azure AD free tier. If you are using P1 or P2 licences you would want to look at using conditional access to perform this (and more) rather than security defaults.
How do Azure AD Security Defaults Work?
Azure AD security defaults are something you need to enable at the tenant level. Once you do this, the rules will apply to all users in your tenant, no exceptions. If you need to enforce rules more selectively or exclude some users then security defaults won’t work for you, you would need to look at getting some P1 licences and using conditional access.
To enable security defaults, you need to go into the Azure AD blade in the portal and go to the properties option. At the bottom of the page, you will find a link called “Manage Security Defaults.”
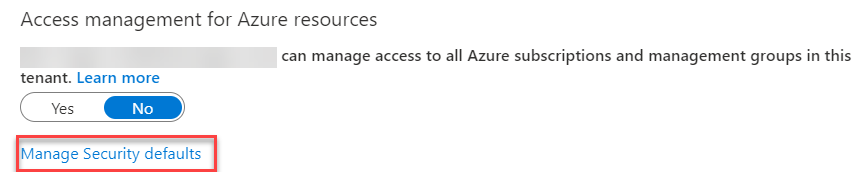
This will take you to a page where you can change security defaults from off, to on. You may find you get a warning about security defaults replacing baseline protections, this is fine.
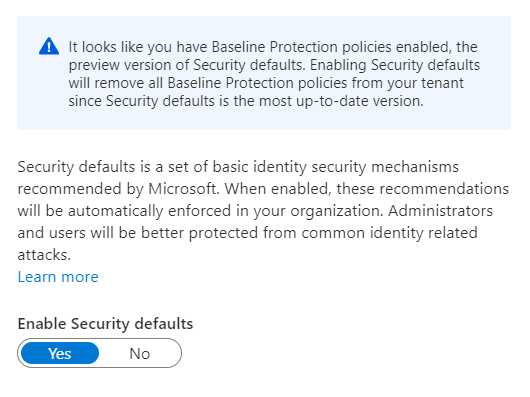
Change this to yes and click save, and security defaults will be enabled. If you find that you need to disable security defaults you can go back into the same window and change enable to “no”.
Now that defaults are enabled you will find several changes take effect:
- Any users who do not have MFA enabled will be prompted to enable it the next time they log in
- When you log in to things like the Azure portal you will now be prompted for MFA
- Any connections you have using legacy authentication will no longer work
Any users in the following Azure AD roles will require MFA every time they sign in to the Azure portal:
- Global administrator
- SharePoint administrator
- Exchange administrator
- Conditional Access administrator
- Security administrator
- Helpdesk administrator
- Billing administrator
- User administrator
- Authentication administrator
Why Would I Want To use Azure AD Security Defaults
The big selling point here is the free MFA. If you are using MFA, you are adding a significant layer of extra protection against password attacks, credential theft, user spoofing etc. In the past this could be somewhat costly, especially for medium-sized organisations with no budget to use Azure AD P1 licences, now you can get this for free.
Alongside MFA, you are also enabling a few defaults which will make you more secure, and in the past would have required conditional access. Disabling legacy authentication is a no-brainer if you are not using it, and immediately removes an attack vector on your tenant.
What Issues does Azure AD Security Defaults Have
The service its self doesn’t really have any issues as such, but it does have several restrictions that you should be aware of before you implement it.
Firstly, as I have mentioned, these settings apply to all users in your tenant. You cannot exclude using from enabling MFA or disabling legacy authentication, it is all or nothing.
Secondly, there are limitations on how you can do MFA. The MFA version provided with security defaults only supports using the mobile application, either as a notification or as a verification code from the app. Security defaults do not support text message, phone calls or app passwords. I would argue that the mobile app option is the most secure, but if you need the other options, then you will need to get P1 licences instead.
Finally, a slightly annoying issue that is the same with conditional access is that your users will show as “disabled” on the MFA status page. Because you’ve enabled MFA with policy, rather than explicitly turning it on for that user, it does not show in the status page. Not a huge deal, given that you know it is enabled for all users, but annoying.
If you do find the limitations above are show-stoppers for you, then you may want to look at conditional access. This is a much more powerful tool that allows you to apply policies enforcing specific settings for specific users. This does require you purchase Azure AD P1 licences.

