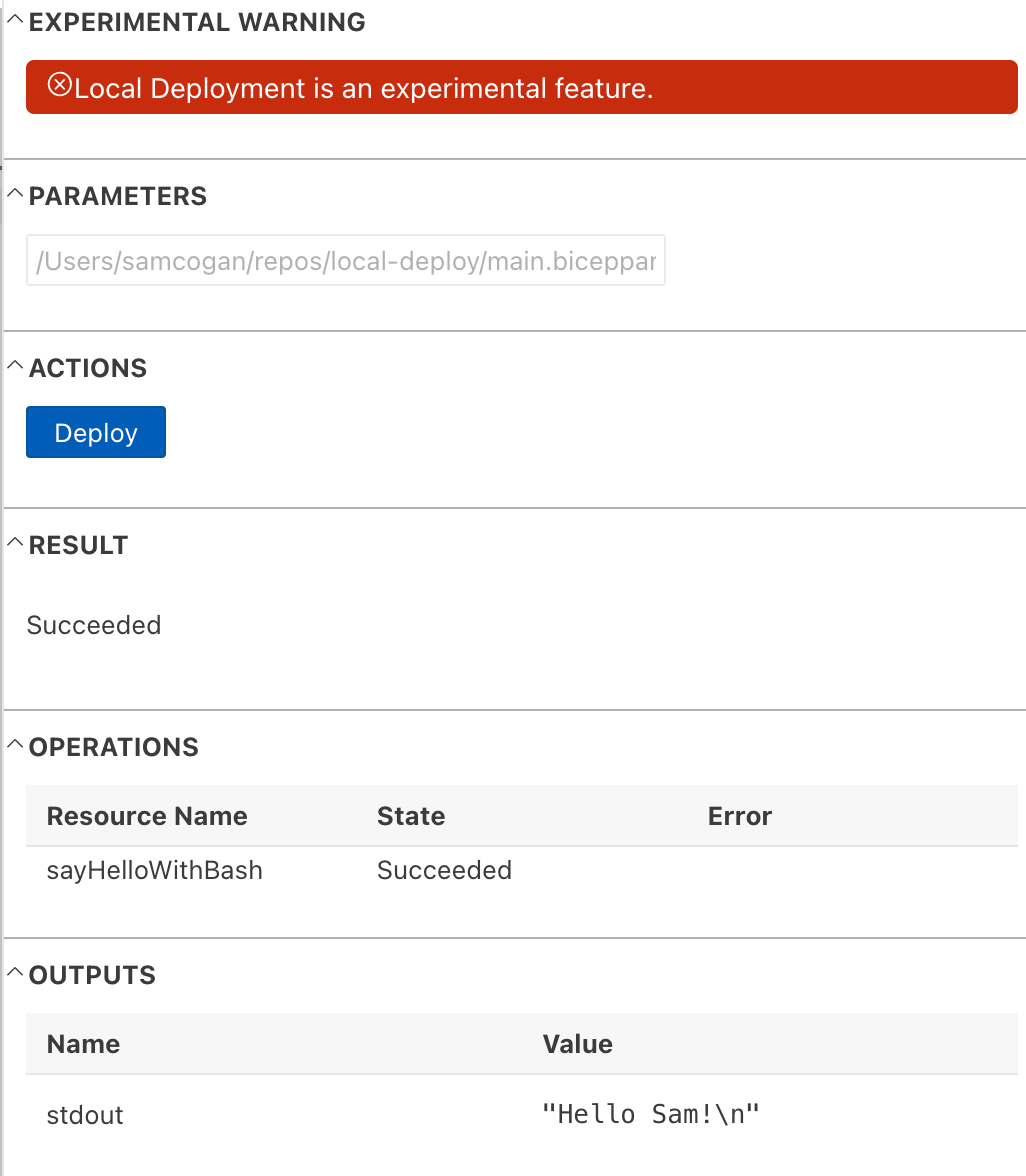
Local Deploy is a new Bicep feature that lets you deploy Bicep code, without connecting to Azure - Crazy!

Bicep is 5 years old! Let’s take a look back at how this all started.

The Pulumi Azure Native SDK has shrunk by 75%, here’s why and what that means for you.
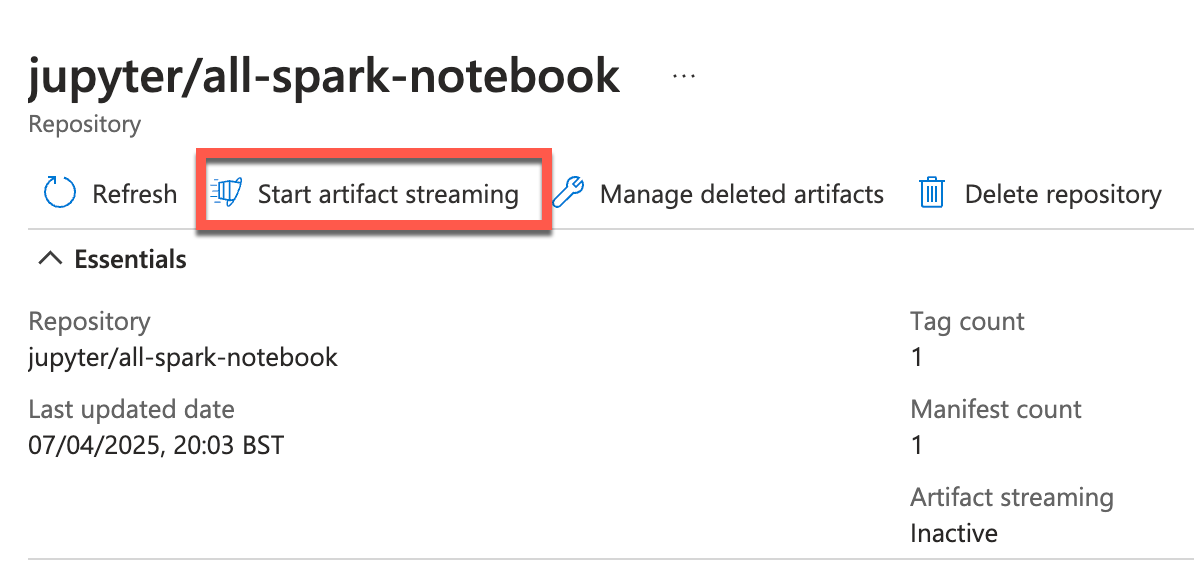
Large container images can slow down deployments and scaling. Artifact streaming can help speed this up.

It’s the end of an era as I hang up my MVP award.
Despite being old and slow in the past, coax is making a comeback as a networking option and it saved my home network from terrible speeds!

How to create Entra ID groups inside an Administrative Unit with Infrastructure as Code and limited permissions
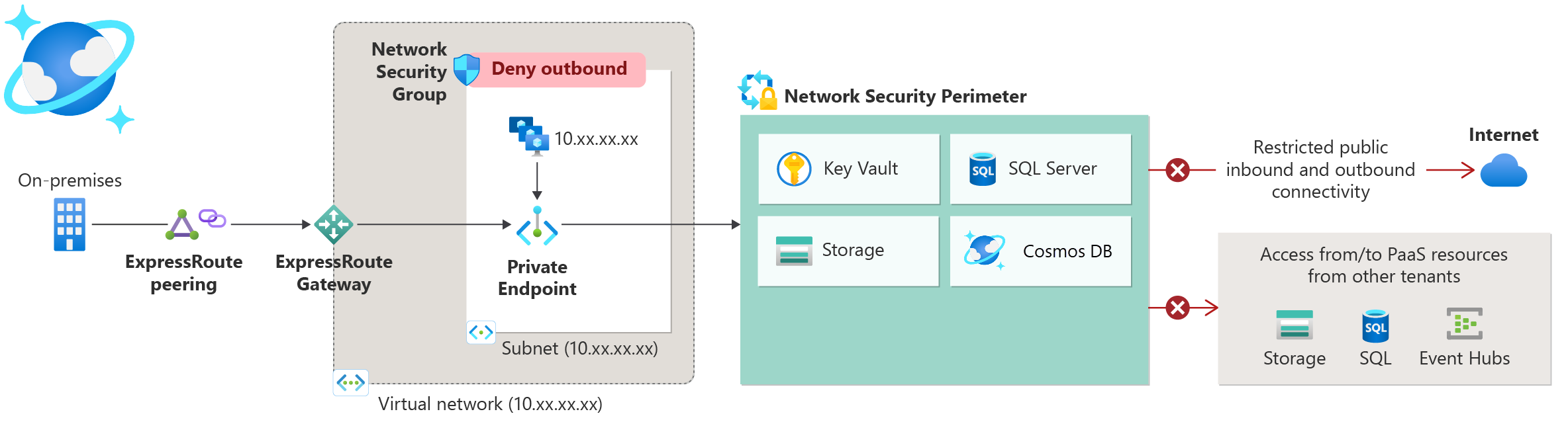
Network Security Perimeter is a new preview feature that helps you apply network security protections to your PaaS resources
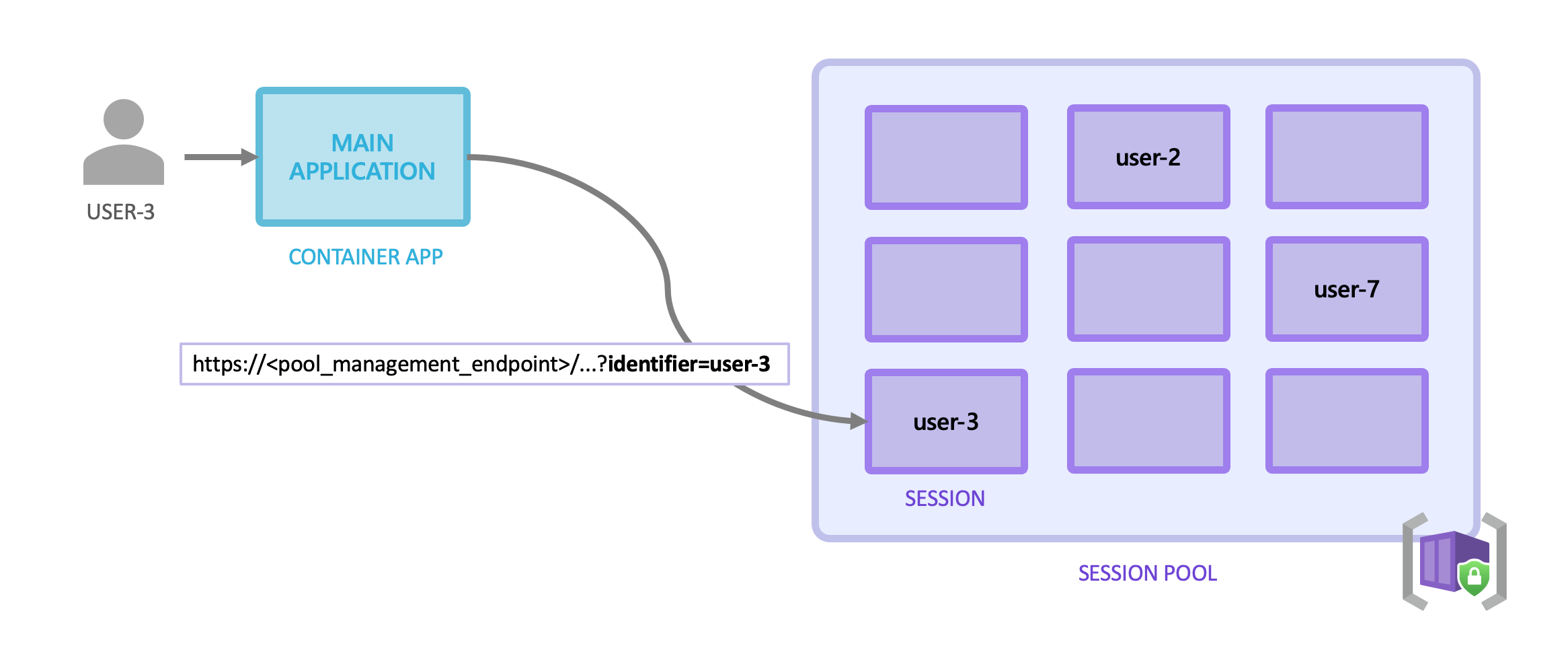
Dynamic Sessions for Azure Container Apps provides a way to run untrusted code in a secure, sandboxed environment with dynamic scaling.
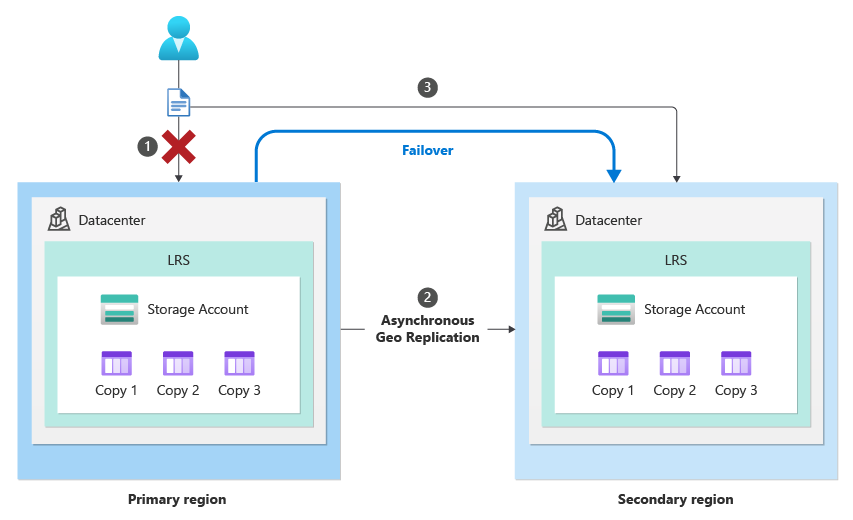
Planned failover for Azure Storage is now in preview, but what is it and how does it differ from unplanned failover?










