Forcing HTTPS with Azure Front Door Rules
Azure Front Door is an excellent solution for providing global load balancing, local ingress and a web application firewall. However, one area of frustration was being able to use it to force HTTP traffic to redirect to HTTPS, it was kind of possible with creating additional routes, but it was a pain. This has changed now with the release of the new rules engine for Front Door.
The Front Door rules engine allows you to create rules that control the routing of your traffic in Front Door with a set of configurable rules that are triggered after your WAF but before the Front Door routes. With these rules, we can do several useful things like adding headers, route to different apps based on browser settings, redirect clients to new hosts, or redirect to using HTTPS.
For the rest of this article, we will be looking at using the rules engine to redirect all traffic to HTTPS.
Pre-Requisites
The rules engine is now enabled on all Azure Front Door instances; there is no need to enable it. The only pre-requisite you need is a Front Door instance setup to deliver traffic to your application.
Creating Rules
To create a new rule, go to the new “Rules Engine Configuration” tab in the portal.
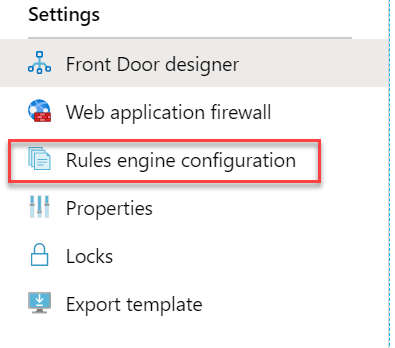
On the page that opens, click the “Add” button, which opens the new rule wizard. We need to give the rule a name then we need to create the rule. The rule consists of two things:
- The condition when the rule is triggered
- What to do when the rule is triggered
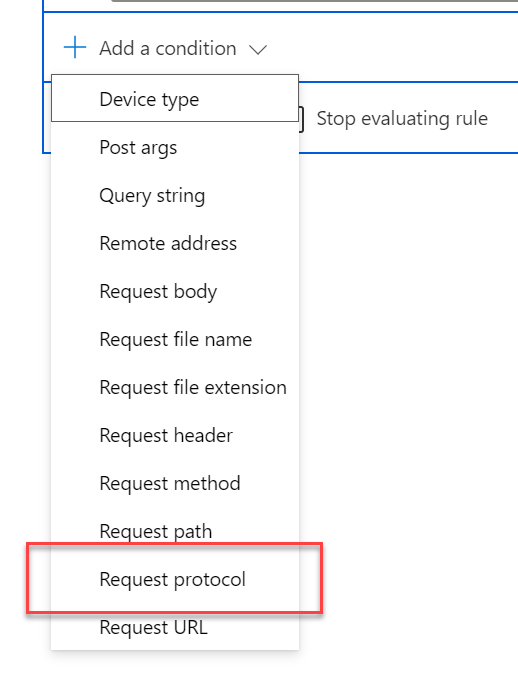
Trigger Condition
First, we will add a trigger condition by clicking the plus button in the condition section. We need to select what property we want to use in the condition, for our needs we need to look at “Request Protocol”.
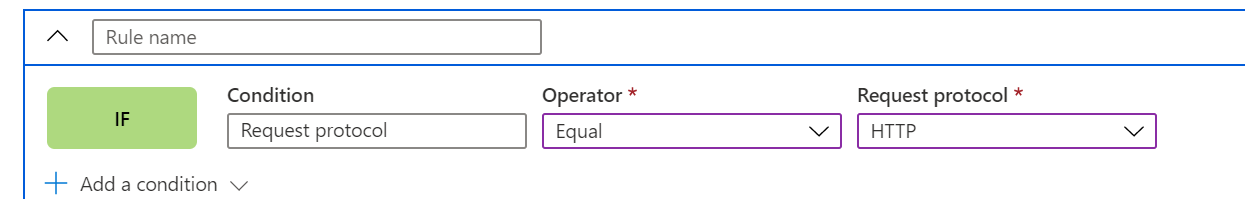
We’ll then complete the rule to trigger when the request protocol is equal to “HTTP”.
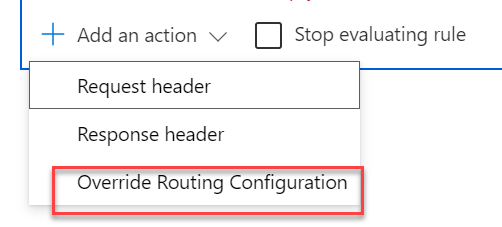
Action
Now we have a trigger for the rule we need to set what we are going to do when it is triggered. We 3 options, change the request header, the response header or overriding the routing rule. In our case, we want to override the routing rule to send the user back to the HTTPS URL.
We then want to configure a 302 redirect that sends the user back to Front Door, but the critical thing is to set “Redirect Protocol” to HTTPS to ensure that the user is forced to use HTTPS.
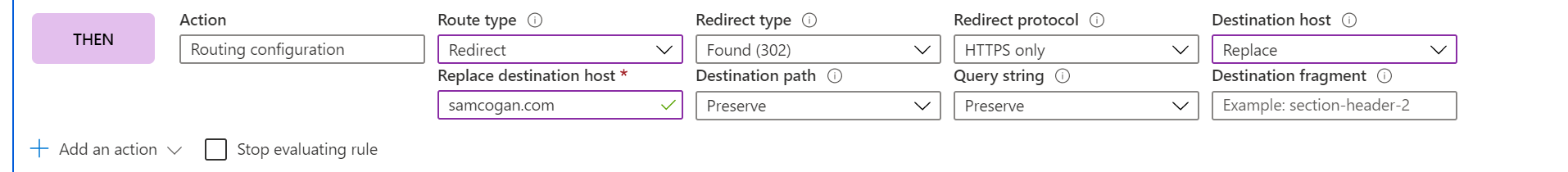
Our final rule looks like this:
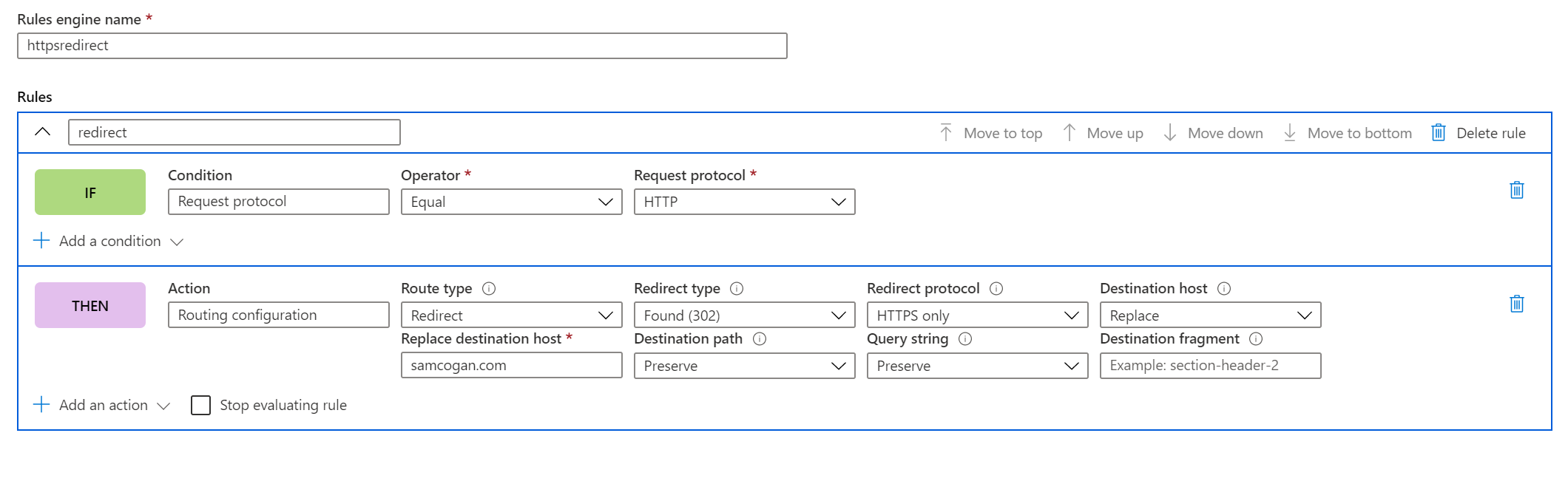
Assign Rule
Currently, our rule won’t do anything as we haven’t assigned it to a Route in Front Door. To assign the rule, we can go to the Front Door designer and locate the route where we want the rule applied. In the Route Details section, you should see a “Rules Engine configuration” drop-down where you can select the rule you created.
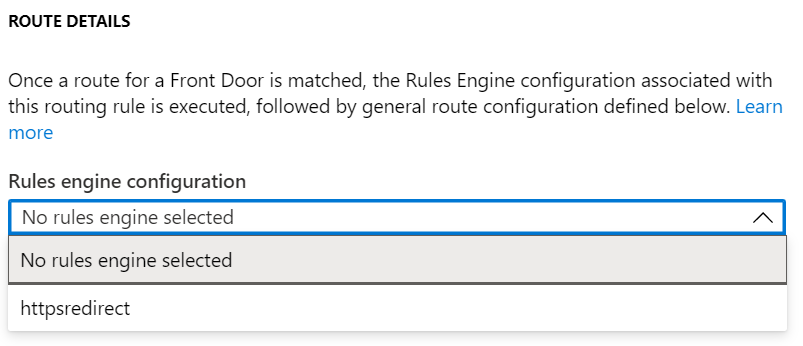
Once we save this assignment, we should see that traffic that is using that route is now redirected to HTTPS.
Note that you can only assign one rules engine to a route, but your rules engine can have multiple rules in it.

