Add IP Restrictions to Azure Container Apps
A new preview feature has just been added to Azure Container Apps (ACA), which allows you to specify IP restrictions. This is a feature most other Azure services offer in one form or another, so it’s great to see this come to ACA. This feature allows you to provide both IP allow and deny lists depending on your preferred approach. This is useful if you want to lock down your apps to specific corporate IP ranges or similar, but it’s also beneficial if you want to put your apps behind something like API Manager. Using these restrictions, you can allow access only to the APIM instance IP and deny everything else. This stops someone from bypassing APIM if they figure out your ACA URL or IP.
IP restrictions are configured per application in your ACA environment, so you can have different IP restrictions for other apps in the same environment if you wish.
IP Restrictions in the Azure Portal
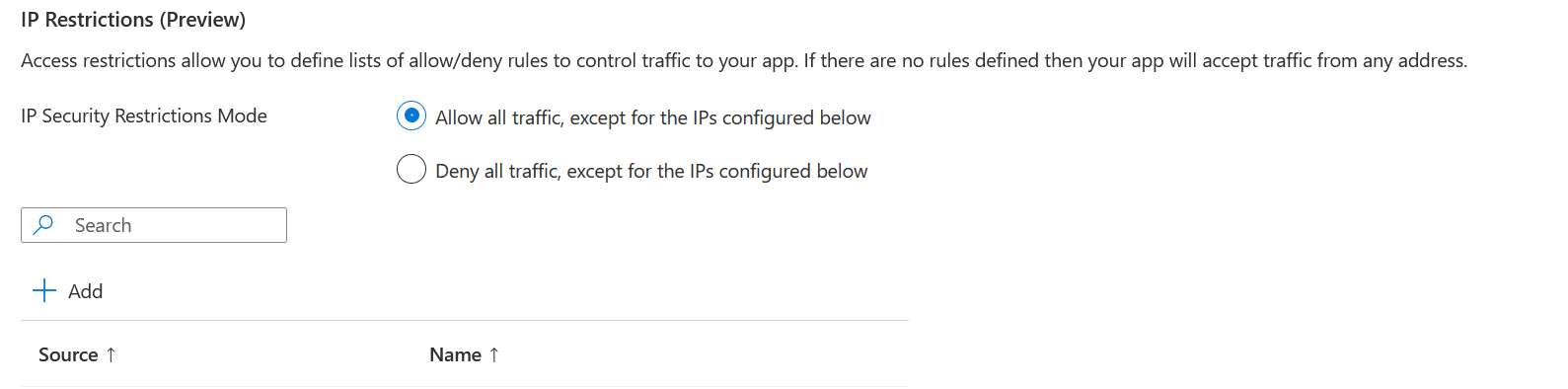
You can configure IP restrictions in the portal by going to the ACA App instance (not the environment) and the “Ingress” tab. Scroll down to the bottom and see the “IP Restrictions” section. Decide whether you create a deny or allow list, and then click the plus button to add IPs or IP ranges.
IP Restrictions in Infrastructure as Code
Bicep
To enable this in Bicep, you need to use the 2022-06-01-preview version of the resource.
resource acaApp 'Microsoft.App/containerApps@2022-06-01-preview' = {
...
"properties": {
"configuration": {
"ingress": {
"ipSecurityRestrictions": [
{
"ipAddressRange": "21.19.4.0/24",
"action": "Allow"
},
{
"ipAddressRange": "91.4.0.0/16",
"action": "Allow"
}
]
}
}
}
}
Terraform
Terraform still doesn’t support Azure Container Apps in its AzureRM provider, so you will need to use the AzApi provider, which is a thing wrapper around the ARM API.
resource "azapi_resource" "aca" {
type = "Microsoft.App/containerApps@2022-03-01"
parent_id = azurerm_resource_group.rg.id
location = azurerm_resource_group.rg.location
name = "acaapp01"
body = jsonencode({
properties: {
managedEnvironmentId = azapi_resource.aca_env.id
configuration = {
ingress = {
external = true
targetPort = 443
ipSecurityRestrictions = [
{
ipAddressRange = "21.19.4.0/24",
action = "Allow"
},
{
ipAddressRange = "91.4.0.0/16",
action = "Allow"
}
]
}
}
...
}
})
}
Pulumi
Pulumi has native support for ACA but will default to the current GA API version, so you will need to specify the API version in your code. The below code is C#, but the same approach will work for other languages.
using Pulumi;
using Pulumi.AzureNative.Resources;
using Pulumi.AzureNative.Storage;
using Pulumi.AzureNative.Storage.Inputs;
using System.Collections.Generic;
using Pulumi.AzureNative.App.V20220601Preview;
using Pulumi.AzureNative.App.V20220601Preview.Inputs;
return await Pulumi.Deployment.RunAsync(() =>
{
var aca = new ContainerApp( "acaapp01", new ContainerAppArgs{
...
Configuration = new ConfigurationArgs{
Ingress = new IngressArgs{
IpSecurityRestrictions = {
new IpSecurityRestrictionRuleArgs{
Action = Pulumi.AzureNative.App.V20220601Preview.Action.Allow,
IpAddressRange = "21.19.4.0/24"
},
new IpSecurityRestrictionRuleArgs{
Action = Pulumi.AzureNative.App.V20220601Preview.Action.Allow,
IpAddressRange = "91.4.0.0/16"
}
}
}
}
});
});

